Setting Up a SOC Aligned with Your IT Operations

Before diving into the details of setting up a SOC (Security Operations Center), let's first address a taboo subject: not all companies have the means and resources to build an internal SOC.
The reality is that unless you are the IT manager of a large, complex organization, it is much more advantageous to partner with a managed security service provider (MSSP). Building a SOC from scratch requires significant investment and considerable resources.
 Did You Know?
Did You Know?
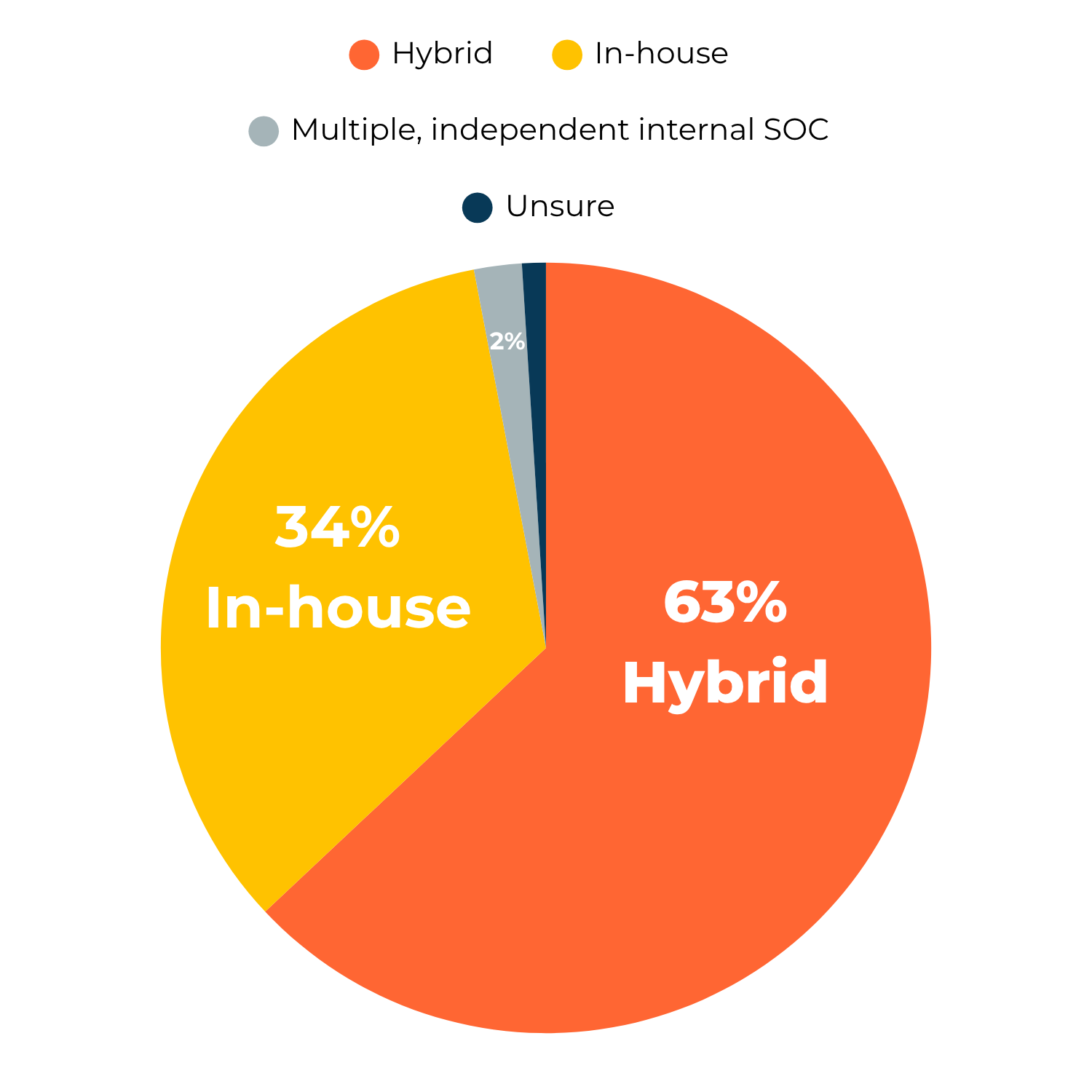
According to a study conducted by Gartner, only 34% of companies choose an internal SOC exclusively, while 63% favor a hybrid approach, combining internal and external resources.
Of course, setting up a SOC is not impossible, provided you know what you have and carefully assess the investment in time, money, and resources that it entails.
Our comprehensive guide will help you understand the basics of an effective SOC, from setting realistic goals to structuring a SOC team, without neglecting policies and technologies. After reading this, you will be able to determine whether it is in your organization's best interest to outsource the SOC or build one internally.
Ready to Accelerate Detection and Response and Promote Continuous Improvement of Your Security Posture?
Book a consultation and ask any questions you may have about our scalable SOC (SEvOC).
Why Is a SOC Essential for Strengthening Your IT Security Strategy?
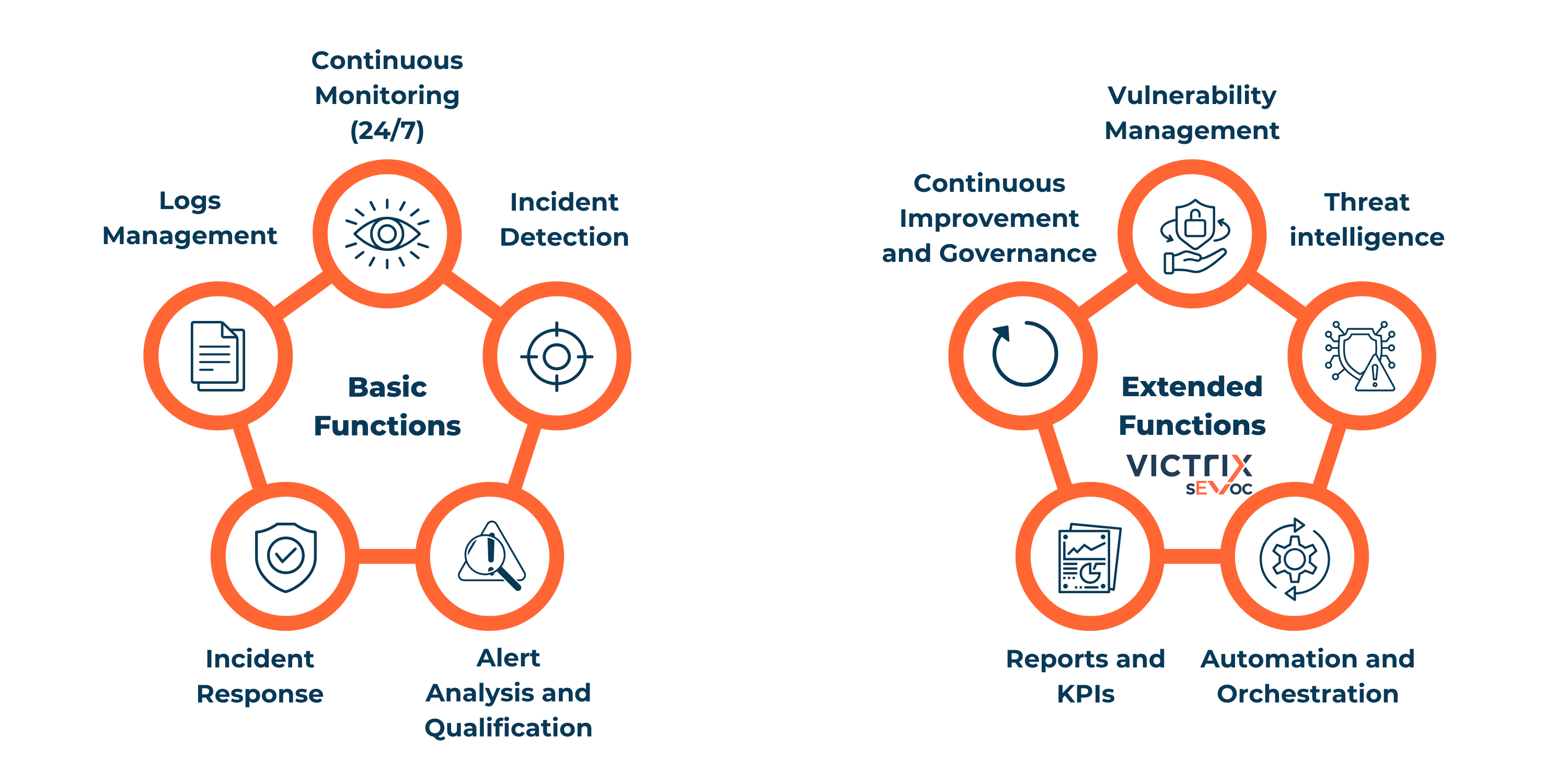
A modern SOC is a strategic asset for any organization seeking to strengthen its security posture. The SOC centralizes key operations such as:
For IT managers, the SOC provides a security framework that allows them to monitor, detect, and respond to incidents with confidence.
Victrix's SEvOC offering stands out by providing a scalable framework that goes beyond the capabilities of a standard SOC. Our offering includes features such as vulnerability management, threat intelligence, automation and orchestration (SOAR), tailored reporting and performance indicators, as well as continuous improvement and governance.
How to Build a SOC: What Your Organization Must Take into Account
Before starting your SOC setup project, it is important to know what you have at your disposal. This is your first hurdle to implementing effective security controls tailored to your needs. Start by asking yourself what is really important to your business.
- What are your critical systems?
- Do you have access to a pool of qualified resources?
- What technologies are you currently using?
- What are your policies, regulations, compliance areas, and contractual obligations?
- What does your attack surface, threat landscape, key malicious actors, and breach history look like?
- What is your organization's overall risk profile?
Only after answering these questions will you be able to choose the relevant controls and identify where to implement them. This will lead you to the resources, logs, and tools you need, the business functions you need to collaborate with, and the network connectivity required for these tools.
Several years could be needed to secure the necessary budget, launch projects, recruit resources, convince management, and begin measuring ROI. You need to be prepared for this possibility and adjust your expectations accordingly.
How to Set Up an Effective SOC Tailored to Your Specific Needs
Set Realistic Goals
Review your processes (vulnerability management, IT asset management, incident management and response, etc.) and standard operating procedures (SOPs). Ask your key stakeholders what they value and where it is located. Set clear goals based on stakeholder expectations and align them with your organization's overall IT security strategy.
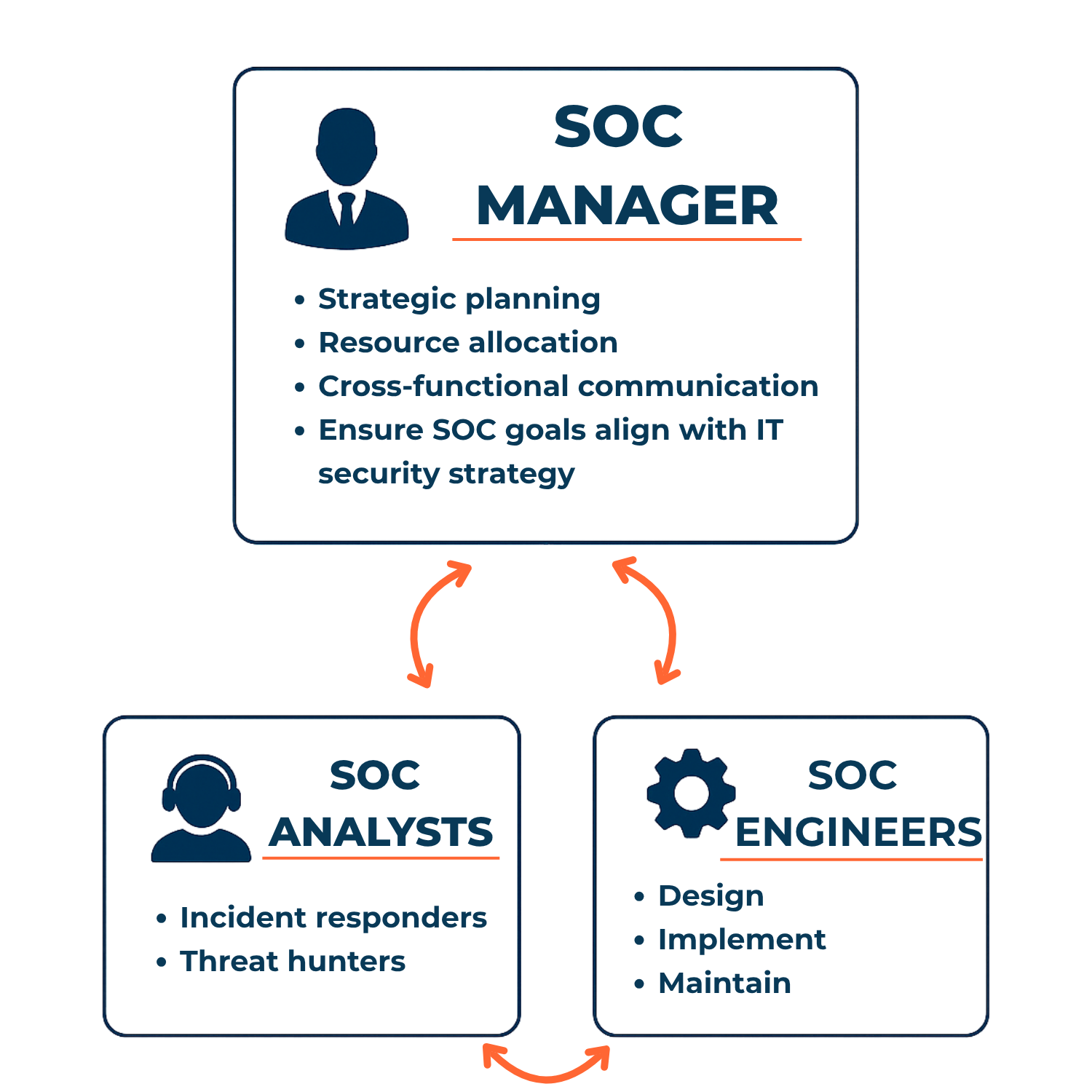
SOC Team Structure: Roles and Responsibilities
If you are looking to build a SOC with limited budget or resources, outsourcing is most likely the only solution that will meet your constraints.
Even for SMEs with more modest needs, the idea of setting up an effective SOC with limited resources is unrealistic, unless you are prepared to bury your resources under an avalanche of security alerts and tedious tasks.
A high-performing SOC team typically includes at least one SOC manager and as many security analysts and SOC engineers as necessary to meet your 24/7/365 monitoring needs. Malicious actors do not limit themselves to regular work shifts (8 to 5), thus justifying the importance of full-time coverage.
Security Policies and Frameworks
Setting up a SOC is part of your compliance strategy. Although the SOC is not responsible for compliance with IT security policies and frameworks (NIST, ISO 27001, Law 25, GDPR, etc.), these frameworks enable the SOC to perform its essential functions.
The Canadian Centre for Cyber Security also recommends integrating threat-based defense into routine security operations, such as those derived from reference frameworks, for example MITRE ATT&CK or OWASP top 10.
Technologies: Choosing the Best Tools to Ensure System Security
- Security Information and Event Management (SIEM)
- Endpoint Detection and Response (EDR)
- Intrusion Prevention System (IPS)
- Security Orchestration, Automation, and Response (SOAR))
- Threat Intelligence Platform (TIP)
- Vulnerability discovery and monitoring
- Incident monitoring, assignment, and documentation
- Sandboxing and malware analysis
- Reporting tools and dashboards
Target Operating Model: Set Up an In-house SOC or Adopt a SOC as a Service (SOCaaS)?
Unless your organization has the means and resources to set up a SOC that operates 24/7, you should definitely opt for an MSSP. Recruiting talent with the right skills, certifications (Comptia+, CISSP, CEH, CISM, CISA, etc.), and expérience in cybersecurity and security incident response is a real challenge, given the labor shortage in the industry.
According to the Cybersecurity Workforce Research Report published by SANS | GIAC in 2025, this marks the first time since discussions about the cybersecurity talent shortage began that organizations have placed more importance on staff with the required skills than on headcount. 52% of IT security leaders identify “lack of qualified personnel” as their main challenge, compared to 48% who cite “their workforce.”
This is also why, according to a study by Gartner, the most common SOC operating model is the hybrid approach, chosen by nearly two-thirds (63%) of companies.
How Does a Managed SOC Differ from an Internal SOC?
Pros and Cons of Each Operational Model |
||
|---|---|---|
| In-house SOC | Managed SOC | |
Access to Qualified Personnel |
Pros You retain complete control over roles, recruitment, and training to strengthen skills or certify your staff |
Pros Instant access to qualified and certified experts |
| Cons You face a shortage of cybersecurity talent, the challenge of finding qualified personnel, and the investment in time, resources, and capital that this entails |
Cons No control over teams or training priorities |
|
Compliance |
Pros A compliance approach aligned with your internal policies |
Pros Providers generally comply with relevant norms (ISO, NIST, Law 25, etc.) |
| Cons Your internal team is responsible for keeping up to date with regulatory changes |
Cons You must validate your provider's certifications |
|
Security Monitoring |
Pros
|
Pros
|
Cons
|
Cons
|
|
Response Time |
Pros You benefit from direct coordination with your internal teams, which speeds up decision-making |
Pros Accelerated sorting through proven processes and automation |
| Cons You depend on your internal capacity and the availability of your resources, which can lead to delays |
Cons In cases where coordination with the customer is necessary, certain delays are to be expected |
|
Cost |
Pros None, it is virtually impossible to spend less than a managed service if you opt for a 24/7 service |
Pros Predictable monthly costs |
| Cons Your initial investment is high to recruit talent, purchase the right security tools, and set up infrastructures |
Cons Evolving needs may result in additional costs |
|
Technologies |
Pros The freedom to choose and manage your favorite tools |
Pros The tools are managed, maintained, and updated by your MSSP |
Cons
|
Cons Limited flexibility in the choice of tools |
|
Visibility |
Pros High transparency, everything is within the company |
Pros Standardized reports, dashboards, and alerts |
| Cons Lack of real-time visibility across all environments |
Cons
|
|
Control and personalization |
Pros You have complete control over configurations and processes |
Pros Easier to manage thanks to predefined frameworks |
| Cons You must perform continuous internal updates to keep the SOC up to date |
Cons May have limited flexibility for customizing workflows |
|
Implementation and Go-Live Phase |
Pros You have complete control over the timing and integration methods |
Pros Rapid deployment with an experienced SOC provider |
| Cons Your onboarding times are longer for new hires or internal changes |
Cons Time required to align with internal systems |
|
Scalability |
Pros Your growth depends on your internal policies |
Pros Easier adaptation by adjusting the service level agreement (SLA) |
| Cons Change requires more recruitment, training, and infrastructure |
Cons The change may result in additional costs or modifications to the contract |
|
How to Choose Your SOC Service Provider?
Aligning Services with Your Environment and Risks
Ensure that your provider understands your industry, regulatory environment, and internal processes. Review the scope of the SLA, including what is monitored, response times, and responsibilities.
Scalability
Is your SOC provider able to adapt to your growth? New sites, hybrid cloud computing, shared environments, without delays or significant costs?
Technologies and Integrations
Check which SIEM, SOAR, and detection technologies are used and how well they integrate with your existing infrastructure.
Data Storage, Usage Rights, and Retention Policies
Know where your sensitive data is stored, how it can be accessed or shared, and what compliance guarantees (ISO, SOC2, GDPR, Law 25) are in place.
You do not need to build a SOC. You need a scalable SOC.
SEvOC stands for more effective detection, smarter responses, and scalable operations. Let's work together to define the SOC model that's right for your organization.

